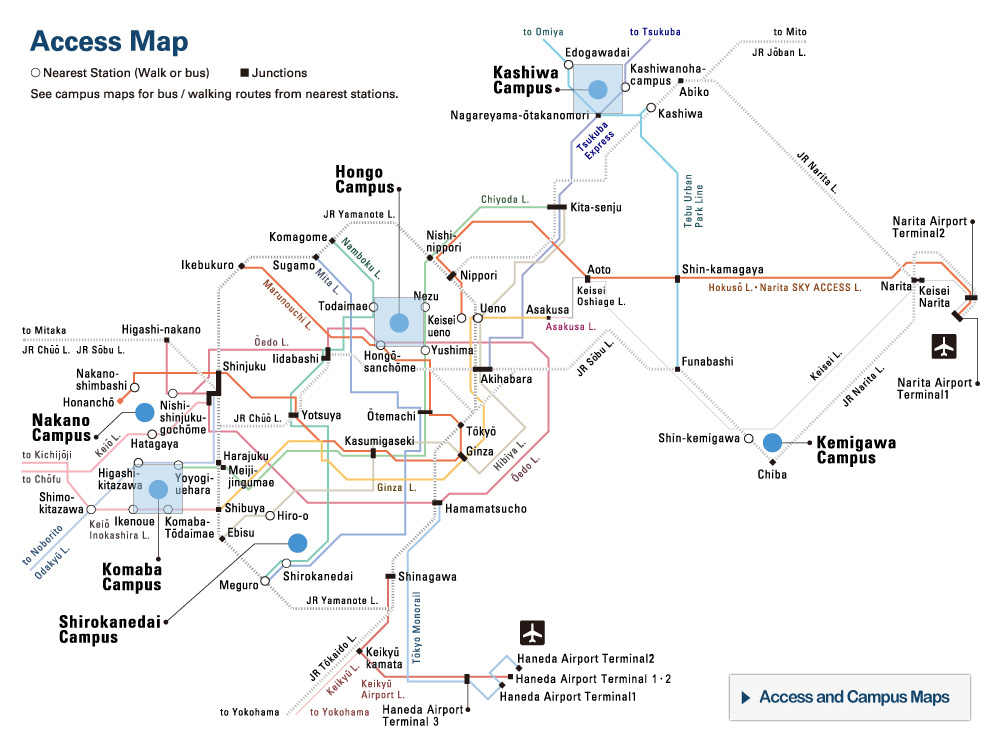
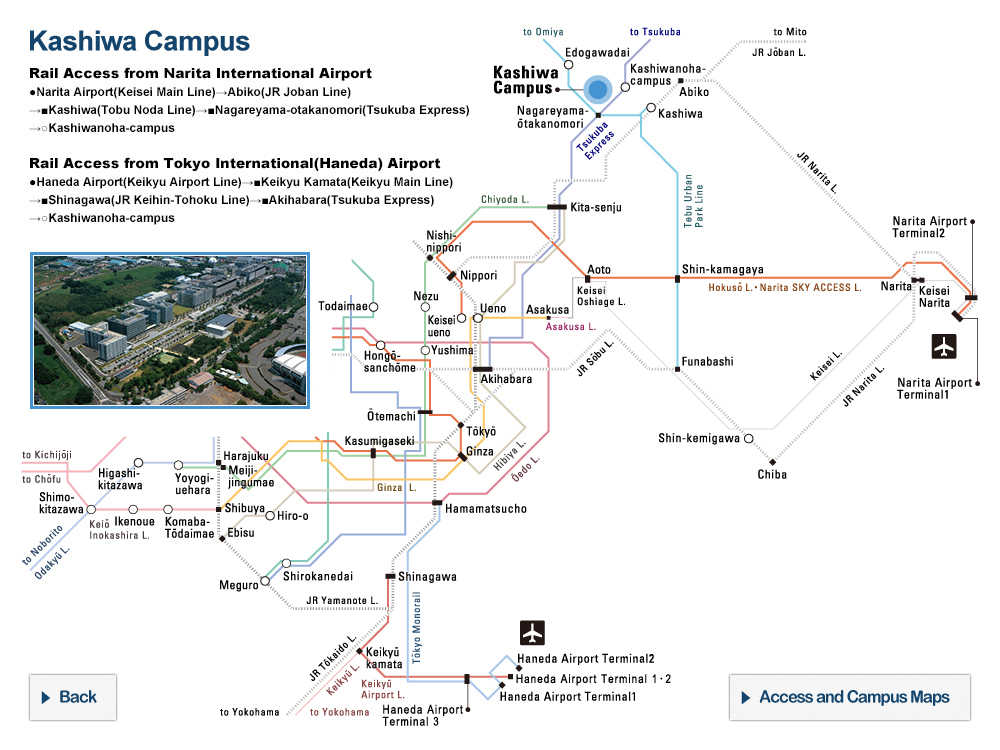
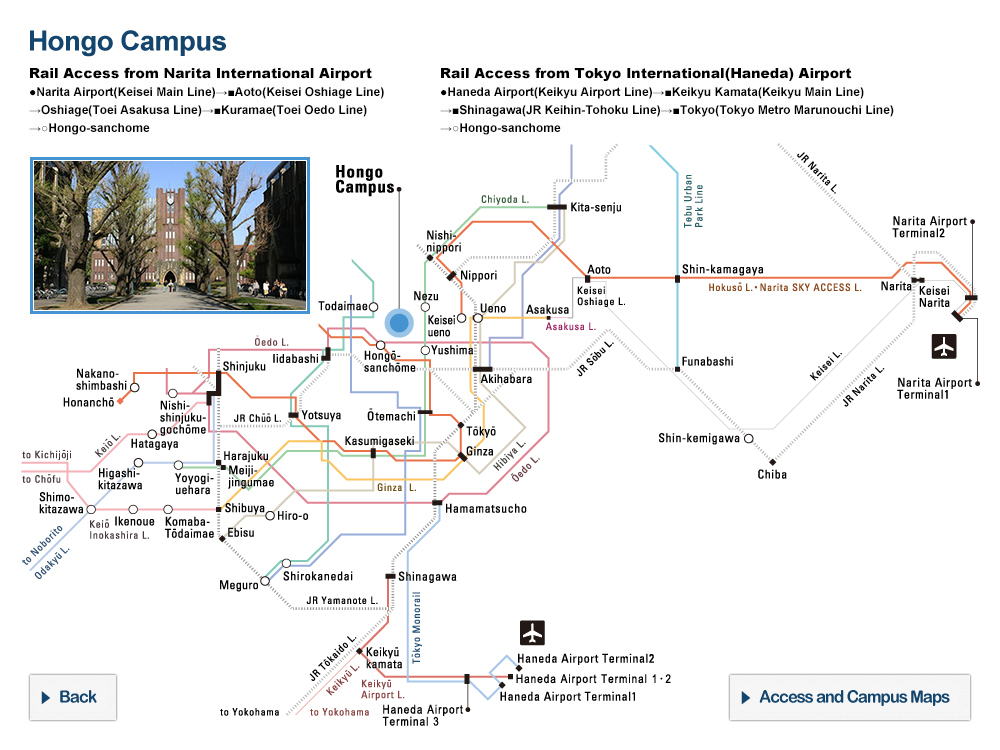
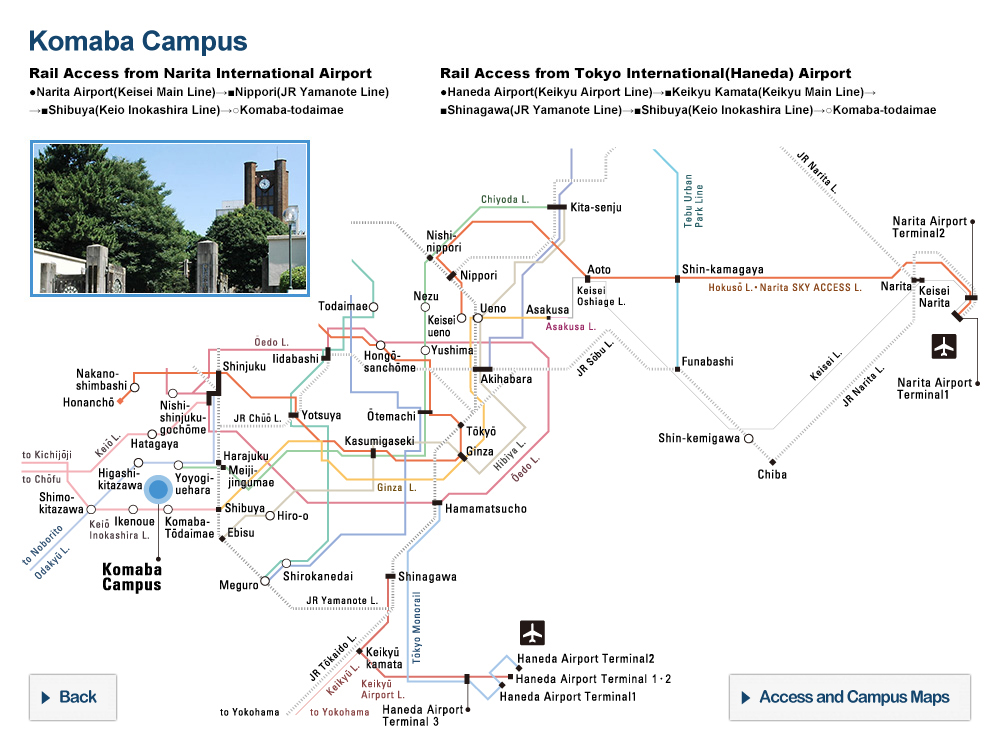
1. Basic Principle on Information Security
To fulfill our mission to advance humanity by conducting robust research and education in the highly information-driven society of the 21st century, the University of Tokyo (hereafter UTokyo) must not only maintain its information infrastructure but also ensure the security of its information assets. The Information Security Policy stipulates necessary rules to ensure information security, consisting of the Basic Policy and the Standards for Information Security Measures. Furthermore, specific procedures are defined to ensure reliable implementation of the Information Security Policy. These measures are intended to raise awareness of the importance of information security among all users of UTokyo, and ensure the security of all information assets owned by the University.
2. Scope of the Information Security Policy
The target users and assets of the Information Security Policy are as follows:
Users
Executives, full-time and part-time faculty and staff, students, research students (including auditing students), and other individuals approved to access information assets owned by UTokyo (collaborators, visitors, external contractors, etc.).
Assets
All information assets owned by UTokyo, including “information” and “information systems”. All types of media (magnetic, optical, printed, etc.) storing information are subject to this policy, including magnetic discs, flash drives, and handwritten notes, among others. For the time being, specimens such as DNA samples are not subject to this policy. Information systems refer to any system that handles information. They include electronic systems as well as systems that handle printed materials such as campus mail. This policy is applicable to all university-owned information assets even if they are stored in information systems outside UTokyo.
The UTokyo Information Security Policy has four main objectives:- Classification and thorough management of information assets owned by UTokyo based on their level of importance
- Defense against breaches targeting information assets owned by UTokyo
- Prevention of harmful acts against information assets owned by UTokyo
- Implementation of early detection and prompt handling of security breaches at UTokyo
3. Basic Policy on Information Security
3.1. Organization and management framework
The Chief Information Security Officer (hereafter CISO) oversees the entire University. The CISO makes comprehensive decisions related to information security and is responsible for information security both within and outside UTokyo. The CISO sets forth information security measures and has the authority to take steps necessary to enforce them across the University. CISO may organize necessary setups for this purpose.
3.2. Information Security Policy and Implementation Procedures
Information security reviews shall be periodically conducted to assess the current state of information asset management. Risk analysis shall be performed to establish the Standards for Information Security Measures and the Implementation Procedures. They shall be reviewed periodically.
3.3. Classification and management of information
Information shall be classified and an appropriate information management method shall be defined.
3.4. Information security of information systems
Management methods shall be defined for information systems.
3.5. Clarification of information security requirements
Information security requirements shall be defined to prevent destruction, damage, tampering, or unauthorized use of information assets, as well as service interruptions or suspension of services caused by unauthorized access, from inside or outside the University.
3.6. Human factors in information security
Rules and procedures shall be developed to ensure that the Information Security Policy is observed. In addition, education and training shall be conducted to raise awareness of and promote compliance with the Information Security Policy.
3.7. Response to information security event
Protocols shall be established to handle information security events (potential incidents and failures related to information security).
3.8. Measures against violation of the Information Security Policy
Rules shall be established to process suspected or actual violations of the Information Security Policy.
3.9. Public relations and information desk for inquiries and complaints
A system for public communications and a contact point for inquiries and complaints shall be established.
3.10. Self-assessments and information security auditing
The processes for self-assessments and information security auditing shall be determined.
3.11. Proactive security reviews
Measures shall be implemented for proactive security reviews.
3.12. Information security budget
Procedures for budget proposals related to university-wide information security shall be established.
3.13. Exceptional cases
Measures to handle exceptional cases shall be established.